PKI Trust Auditor – User Guide
Table of Contents
Toggle
Table of Contents
ToggleIntroduction & Overview
What is PKI Trust Auditor?
The PKI Trust Auditor is a comprehensive security auditing tool for Active Directory Certificate Services (ADCS) infrastructure. It provides automated discovery, assessment, and reporting of your PKI environment’s security posture.
Key Features
- Automated CA Discovery: Automatically discovers all Certificate Authorities in your Active Directory environment
- Comprehensive Auditing: Performs connectivity, configuration, template, cryptographic, and operational audits
- Multi-Format Reporting: Generates JSON, CSV, web-based, and console reports
- Interactive Interface: User-friendly console menu system with color-coded output
- Parameter-Driven Configuration: Customizable audit settings via parameters.json
- Evidence Collection: Detailed evidence files for each control execution
- Web Application: Interactive web-based reporting with visualizations
Target Audience
- PKI Administrators: Monitor and maintain certificate authority health
- Security Professionals: Assess PKI security posture and compliance
- Compliance Auditors: Generate evidence for regulatory requirements
- IT Operations: Troubleshoot PKI infrastructure issues
System Requirements & Installation
Prerequisites
- .NET 9.0 or later runtime
- Windows environment with Active Directory connectivity
- Domain User Account with appropriate permissions:
- Read access to Active Directory
- WMI and PowerShell remoting rights to CA servers
- Certificate Authority administrative permissions
- Network Connectivity to Certificate Authority servers
Installation Steps
Option 1: Use Executable
# Run the application
PKI_Trust_Auditor.exe
Required Permissions
- Active Directory: Read access to Configuration container
- Certificate Authorities:
- Local Administrator on CA servers (for WMI/PowerShell)
- CA Administrator or Certificate Manager permissions
- Network: TCP ports 135 (WMI), 5985/5986 (WinRM)
Getting Started
First Run – Interactive Mode
Run the application without arguments to access the interactive menu:
PKI_Trust_Auditor.exe
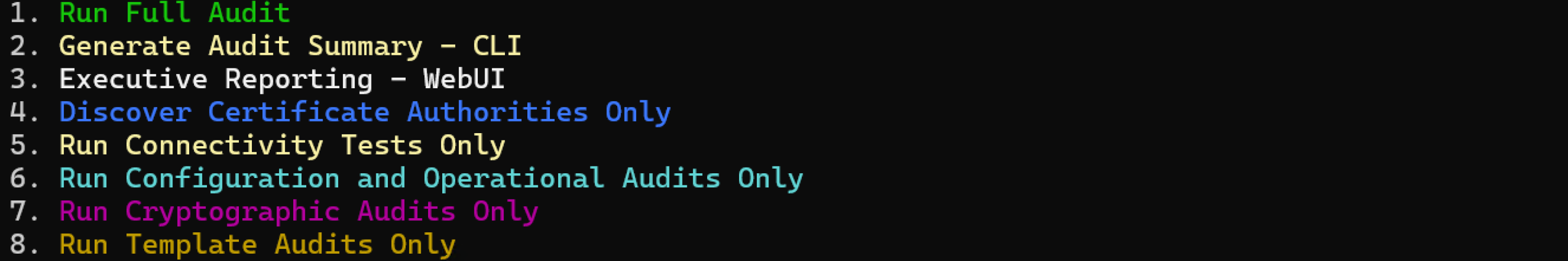
You’ll see the main menu with color-coded options:
===============================================================================
================= PKI TRUST AUDITOR | https://securetron.net =================
Active Directory Certificate Authority Infrastructure & Security Auditing Tool
===============================================================================
Main Menu:
1. Run Full Audit
2. Generate Audit Summary - CLI
3. Executive Reporting - WebUI
4. Discover Certificate Authorities Only
5. Run Connectivity Tests Only
6. Run Configuration and Operational Audits Only
7. Run Cryptographic Audits Only
8. Run Template Audits Only
9. Exit
Command Line Options
Run specific operations directly from command line:
# Display help
PKI_Trust_Auditor.exe --help
# Run specific audit tests
PKI_Trust_Auditor.exe --tests config
PKI_Trust_Auditor.exe --tests crypto
PKI_Trust_Auditor.exe --tests templates
PKI_Trust_Auditor.exe --tests connectivity
PKI_Trust_Auditor.exe --tests full
# Launch web application
PKI_Trust_Auditor.exe --report
# Clear audit results cache
PKI_Trust_Auditor.exe --clear
# Display version information
PKI_Trust_Auditor.exe --version
Parameters Configuration
Create or modify parameters.json to customize audit behavior:
{
"DomainOverride": "DC=yourdomain,DC=com",
"CA-CRYPTO-001": 2048,
"CA-CRYPTO-002": ["MD5", "SHA1", "DES", "RC4", "3DES"],
"CA-TEMPLATE-001": true,
"CA-OPS-002": ["10", "3", "5", "1"]
}
Audit Controls Reference
Connectivity Tests
PKI-TEST-001: WMI/SMB Connectivity Test
- Severity: Critical
- Purpose: Tests basic network connectivity to Certificate Authorities
- Method: WMI service connectivity and SMB file sharing
- Expected Result: Successful WMI/SMB connection to CA
- Evidence: Connectivity method and reachability status
- Recommendation: Check network connectivity, firewall rules, and WMI service status
PKI-TEST-002: PowerShell Connectivity Test
- Severity: Critical
- Purpose: Tests PowerShell remoting capability (fallback if WMI fails)
- Method: PowerShell remoting via WinRM
- Expected Result: Successful PowerShell remoting to CA
- Evidence: Connectivity method and reachability status
- Recommendation: Enable PowerShell remoting and check WinRM configuration
PKI-TEST-003: User Privilege Validation
- Severity: Critical
- Purpose: Validates current user has appropriate privileges
- Method: Checks user permissions and group membership
- Expected Result: User has required administrative privileges
- Evidence: User identity and privilege assessment
- Recommendation: Run with appropriate administrative credentials
Configuration Audits
CA-CONFIG-001: CA Registry Configuration
- Severity: High
- Purpose: Retrieves comprehensive CA registry configuration
- Method: Remote registry queries via WMI/PowerShell
- Expected Result: Complete CA registry configuration retrieved
- Evidence: JSON file with all registry values and settings
- Recommendation: Review registry configuration for security settings
CA-CONFIG-002: CA Templates
- Severity: High
- Purpose: Discovers and analyzes certificate templates
- Method: certutil commands and template analysis
- Expected Result: List of all certificate templates with configurations
- Evidence: Template names, settings, and security descriptors
- Recommendation: Review template security and remove unnecessary templates
CA-CONFIG-003: AIA Configuration
- Severity: High
- Purpose: Analyzes Authority Information Access configuration
- Method: certutil -getreg CA\CSP\AIA
- Expected Result: AIA URLs and configuration settings
- Evidence: AIA URLs, AddToCertificateAia, AddToCertificateOcsp flags
- Recommendation: Ensure AIA URLs are accessible and properly configured
CA-CONFIG-004: CRL Distribution Points
- Severity: High
- Purpose: Examines CRL Distribution Point configuration
- Method: certutil -getreg CA\CSP\CRL
- Expected Result: CRL URLs and publication settings
- Evidence: CRL URLs, publication flags, delta CRL settings
- Recommendation: Verify CRL URLs are accessible and properly published
CA-CONFIG-005: CAPolicy.inf Configuration
- Severity: Medium
- Purpose: Retrieves CAPolicy.inf file configuration
- Method: File retrieval and parsing
- Expected Result: CAPolicy.inf settings and policies
- Evidence: CAPolicy.inf content and configuration
- Recommendation: Review certificate policy settings
CA-CONFIG-006: PowerShell Template Export
- Severity: Medium
- Purpose: Exports detailed template configuration via PowerShell
- Method: PowerShell script execution
- Expected Result: Comprehensive template configuration in JSON format
- Evidence: JSON file with detailed template attributes and settings
- Recommendation: Use for detailed template analysis and security review
Operational Audits
CA-OPS-001: CertSvc Service Status
- Severity: High
- Purpose: Checks Certificate Services service status
- Method: Service status query via WMI/PowerShell
- Expected Result: CertSvc service running and healthy
- Evidence: Service status, startup type, and health
- Recommendation: Ensure CertSvc service is running and configured for automatic startup
CA-OPS-002: CA Certificate Expiration Validation
- Severity: High
- Purpose: Validates CA certificate expiration dates
- Method: Certificate retrieval and date analysis
- Expected Result: CA certificates meet configured expiration limits
- Evidence: Certificate validity periods, remaining time, compliance status
- Recommendation: Reissue certificates before expiration or adjust validity periods
CA-OPS-003: CA Certificate AIA Configuration Validation
- Severity: High
- Purpose: Validates AIA extension in CA certificates
- Method: Certificate analysis and extension validation
- Expected Result: Proper AIA configuration in CA certificates
- Evidence: AIA extension presence, URLs, configuration status
- Recommendation: Configure AIA extension with proper URLs
CA-OPS-004: CA Certificate CDP Configuration Validation
- Severity: High
- Purpose: Validates CDP extension in CA certificates
- Method: Certificate analysis and extension validation
- Expected Result: Proper CDP configuration in CA certificates
- Evidence: CDP extension presence, URLs, configuration status
- Recommendation: Configure CDP extension with proper URLs
CA-OPS-005: AIA URL Reachability
- Severity: Medium
- Purpose: Tests accessibility of HTTP-based AIA URLs
- Method: HTTP connectivity testing to AIA URLs
- Expected Result: All HTTP AIA URLs with AddToCertificateAia=TRUE are accessible
- Evidence: URL reachability status, HTTP response codes
- Recommendation: Fix accessibility issues for HTTP AIA URLs
CA-OPS-006: CDP/CRL URL Reachability
- Severity: Medium
- Purpose: Tests accessibility of HTTP-based CDP/CRL URLs
- Method: HTTP connectivity testing to CDP/CRL URLs
- Expected Result: All HTTP CDP/CRL URLs with qualifying flags are accessible
- Evidence: URL reachability status, HTTP response codes, flag analysis
- Recommendation: Fix accessibility issues for HTTP CDP/CRL URLs
CA-OPS-007: AIA Certificate Download and Expiration Validation
- Severity: Medium
- Purpose: Downloads AIA certificates and validates expiration
- Method: Certificate download and expiration analysis
- Expected Result: Downloaded AIA certificates have valid expiration dates
- Evidence: Certificate details, download status, expiration validation
- Recommendation: Update expired AIA certificates
CA-OPS-008: CRL Download and Validation
- Severity: Medium
- Purpose: Downloads CRL files and validates accessibility
- Method: CRL download and basic validation
- Expected Result: CRL files are downloadable and valid
- Evidence: CRL download status, file size, basic validation
- Recommendation: Ensure CRL publication and accessibility
CA-OPS-009: CA Audit Filter Configuration
- Severity: Critical
- Purpose: Validates CA audit filter configuration
- Method: Registry analysis and bitmask validation
- Expected Result: AuditFilter set to 127 for full auditing
- Evidence: Current AuditFilter value, missing audit categories
- Recommendation: Set AuditFilter to 127 to enable all audit categories
Template Audits
CA-TEMPLATE-001: CA Template Restriction Validation
- Severity: Critical
- Purpose: Validates CA template restrictions (CT_FLAG_IS_CA)
- Method: Template flag analysis and consistency validation
- Expected Result: Non-CA templates should not be on ROOT or Intermediate CAs
- Evidence: Template analysis, CT_FLAG_IS_CA status, compliance assessment
- Recommendation: Remove non-CA templates from CA servers or ensure consistent flag usage
CA-TEMPLATE-002: Template Key Size Validation
- Severity: High
- Purpose: Validates minimum key sizes for certificate templates
- Method: Template key size analysis against configured threshold
- Expected Result: All templates meet minimum key size requirement
- Evidence: Template key sizes, compliance status, non-compliant templates
- Recommendation: Update templates to meet minimum key size requirements
CA-TEMPLATE-003: Template Schema Version Validation
- Severity: High
- Purpose: Validates template schema versions against prohibited versions
- Method: Schema version analysis and prohibited version checking
- Expected Result: Templates do not use prohibited schema versions
- Evidence: Template schema versions, prohibited version matches, compliance status
- Recommendation: Update templates to use compliant schema versions
CA-TEMPLATE-004: Template CSP Validation
- Severity: Critical
- Purpose: Validates Cryptographic Service Provider usage in templates
- Method: CSP analysis against approved and prohibited lists
- Expected Result: Templates use approved CSPs and avoid prohibited CSPs
- Evidence: Template CSP usage, compliance status, non-compliant templates
- Recommendation: Update templates to use approved CSPs and avoid prohibited CSPs
CA-TEMPLATE-005: Template Enrollee Supplies Subject Validation
- Severity: High
- Purpose: Validates enrollee supplies subject flag usage
- Method: Flag analysis and exclusion list validation
- Expected Result: Templates with CT_FLAG_ENROLLEE_SUPPLIES_SUBJECT=1 must be in exclusion list
- Evidence: Enrollee supplies subject flag status, exclusion list compliance
- Recommendation: Update templates or exclusion list to maintain compliance
Cryptographic Audits
CA-CRYPTO-001: CA Certificate Key Size Validation
- Severity: High
- Purpose: Validates CA certificate key sizes
- Method: Certificate analysis and key size validation
- Expected Result: CA certificate key size meets minimum requirement
- Evidence: Certificate details, key size, compliance status
- Recommendation: Reissue CA certificate with adequate key size
CA-CRYPTO-002: CA Certificate Weak Algorithm Detection
- Severity: High
- Purpose: Detects weak cryptographic algorithms in CA certificates
- Method: Algorithm analysis against prohibited algorithm list
- Expected Result: CA certificate uses strong cryptographic algorithms
- Evidence: Signature and key algorithms, weak algorithm detection
- Recommendation: Reissue CA certificate using strong algorithms
CA-CRYPTO-003: CA Certificate Extended Key Usage Validation
- Severity: High
- Purpose: Validates Extended Key Usage extensions in CA certificates
- Method: EKU analysis against prohibited EKU list
- Expected Result: CA certificate does not contain prohibited EKUs
- Evidence: EKU extensions, prohibited EKU detection, compliance status
- Recommendation: Reissue CA certificate without prohibited EKUs
CA-CRYPTO-004: CA Certificate Basic Constraints Validation
- Severity: High
- Purpose: Validates Basic Constraints extension in CA certificates
- Method: Basic Constraints analysis against configured values
- Expected Result: CA certificate basic constraints match configured values
- Evidence: CA flag, path length constraint, compliance status
- Recommendation: Reissue CA certificate with correct basic constraints
Permission Audits
CA-PERM-001: CA Administrator Permission Validation
- Severity: Critical
- Purpose: Validates CA administrator permissions against expected principals
- Method: Security permission analysis and principal validation
- Expected Result: All CA administrators are in expected principals list
- Evidence: Admin principals, expected principals, compliance status
- Recommendation: Add non-compliant principals to expected list or remove permissions
Usage Scenarios & Examples
Full Infrastructure Assessment
Run a complete audit of your PKI environment:
# Interactive menu option 1
PKI_Trust_Auditor.exe
# Command line equivalent
PKI_Trust_Auditor.exe --tests full
This executes:
- User privilege validation
- Certificate Authority discovery
- Connectivity testing (WMI/PowerShell)
- Configuration audits (registry, templates, AIA, CRL)
- Operational audits (service status, certificates, URLs)
- Template audits (restrictions, key sizes, schema versions)
- Cryptographic audits (key sizes, algorithms, extensions)
- Permission audits
Targeted Connectivity Testing
Test only network connectivity to discovered CAs:
# Interactive menu option 5
# Or command line
PKI_Trust_Auditor.exe --tests connectivity
Template Security Assessment
Focus on certificate template security:
# Interactive menu option 8
# Or command line
PKI_Trust_Auditor.exe --tests templates
Cryptographic Review
Analyze certificate and algorithm security:
# Interactive menu option 7
# Or command line
PKI_Trust_Auditor.exe --tests crypto
Web-Based Reporting
Generate and launch interactive web reports:
# Interactive menu option 3
# Or command line
PKI_Trust_Auditor.exe --report
Quick Discovery Only
Discover CAs without running audits:
# Interactive menu option 4
# Or command line (no direct equivalent, use interactive menu)
Output & Reporting
File Output Structure
The tool creates an Audit-Results/ directory with the following structure:
Audit-Results/
├── PKI-Audit.json # Complete audit results in JSON format
├── PKI-Audit.csv # Summary data in CSV format
├── CA-CRYPTO-001-{CA-Name}.cer # Downloaded CA certificates
├── CA-OPS-007-{CA-Name}.cer # Downloaded AIA certificates
├── CA-OPS-008-{CA-Name}.crl # Downloaded CRL files
├── {Control-ID}-{CA-Name}.txt # Individual control evidence files
└── {Control-ID}-{CA-Name}.json # JSON evidence files (for some controls)
Report Formats
JSON Report (PKI-Audit.json)
Complete structured data including:
- Certificate Authority details
- All control results with evidence
- Execution timestamps and durations
- Summary statistics and success rates
CSV Report (PKI-Audit.csv)
Tabular data suitable for spreadsheet analysis:
- Control ID, Name, Severity, Status
- Certificate Authority, Expected Result
- Execution time and duration
Individual Control Files
Detailed evidence for each control execution:
- Control metadata and configuration
- Complete evidence text
- Recommendations and compliance status
- Execution details and timing
Web Application
Interactive web-based reporting:
- Visual summary dashboard
- Detailed control breakdown
- Filtering and search capabilities
- Export functionality
Evidence Collection
Each control generates detailed evidence including:
- Control Metadata: ID, name, severity, expected result
- Execution Details: Timestamp, duration, CA information
- Evidence Content: Raw output, parsed data, analysis results
- Compliance Status: Success, failure, error, or not run
- Recommendations: Specific remediation steps
Certificate and CRL Storage
- CA Certificates: Downloaded from Active Directory for analysis
- AIA Certificates: Downloaded from AIA URLs for validation
- CRL Files: Downloaded from CDP URLs for accessibility testing
Troubleshooting & Common Issues
Connectivity Problems
WMI Connectivity Failures
Symptoms: PKI-TEST-001 failures Causes:
- Firewall blocking port 135
- WMI service not running on CA
- Network connectivity issues
- Insufficient permissions
Solutions:
# Check WMI service status
sc \\CA-Server query winmgmt
# Test basic connectivity
Test-NetConnection CA-Server -Port 135
# Verify firewall rules
netsh advfirewall firewall show rule name="Windows Management Instrumentation (WMI-In)"
PowerShell Remoting Failures
Symptoms: PKI-TEST-002 failures Causes:
- WinRM service not running
- PowerShell remoting not enabled
- Certificate issues for HTTPS
- Network connectivity problems
Solutions:
# Enable PowerShell remoting (run on CA server)
Enable-PSRemoting -Force
# Check WinRM service
Get-Service WinRM
# Test WinRM connectivity
Test-WSMan CA-Server
Permission Issues
Active Directory Access
Symptoms: CA discovery failures Causes:
- Insufficient AD permissions
- Domain controller connectivity
- DNS resolution problems
Solutions:
- Ensure domain user account has read access to Configuration container
- Verify DNS resolution for domain controllers
- Check network connectivity to domain controllers
CA Administrative Permissions
Symptoms: Configuration audit failures Causes:
- Missing CA Administrator permissions
- Local administrator rights on CA servers
- Certificate Manager permissions
Solutions:
- Add user to CA Administrators group
- Grant local administrator rights on CA servers
- Ensure Certificate Manager permissions
Configuration Issues
Parameters.json Problems
Symptoms: Control execution errors or unexpected behavior Causes:
- Invalid JSON format
- Missing required parameters
- Incorrect parameter values
Solutions:
// Validate parameters.json structure
{
"DomainOverride": "DC=yourdomain,DC=com",
"CA-CRYPTO-001": 2048,
"CA-CRYPTO-002": ["MD5", "SHA1", "DES", "RC4", "3DES"],
"CA-TEMPLATE-001": true
}
Domain Detection Issues
Symptoms: Unable to discover CAs or retrieve certificates Causes:
- Automatic domain detection failure
- Incorrect DomainOverride setting
- Network/DNS issues
Solutions:
- Verify DomainOverride in parameters.json matches your domain
- Check DNS resolution for domain controllers
- Ensure network connectivity to domain
Performance Issues
Slow Execution
Causes:
- Large number of CAs to audit
- Network latency to remote CAs
- Resource constraints on CA servers
Solutions:
- Run targeted audits instead of full audits
- Schedule audits during off-peak hours
- Ensure adequate resources on CA servers
Memory Usage
Causes:
- Large certificate files
- Extensive evidence collection
- Multiple concurrent audits
Solutions:
- Clear audit results cache regularly
- Monitor system resources during execution
- Consider running on dedicated audit server
Advanced Configuration
Parameters.json Reference
Domain Configuration
{
"DomainOverride": "DC=securetron-lab,DC=local"
}
Cryptographic Settings
{
"CA-CRYPTO-001": 2048, // Minimum key size in bits
"CA-CRYPTO-002": ["MD5", "SHA1", "DES"], // Prohibited algorithms
"CA-CRYPTO-003": ["Server Authentication", "Client Authentication"], // Prohibited EKUs
"CA-CRYPTO-004": ["CA", "-1"] // Basic constraints (CA flag, path length)
}
Template Settings
{
"CA-TEMPLATE-001": true, // Enable template restriction validation
"CA-TEMPLATE-002": 2048, // Minimum template key size
"CA-TEMPLATE-003": [1], // Prohibited schema versions
"CA-TEMPLATE-004": [ // CSP validation settings
"Microsoft Base Cryptographic Provider v1.0", // Prohibited CSPs
"APPROVED", // Separator
"Microsoft Enhanced Cryptographic Provider v1.0", // Approved CSPs
"Microsoft Strong Cryptographic Provider"
],
"CA-TEMPLATE-005": [ // Enrollee supplies subject
"1", // Control enabled (1) or disabled (0)
"WebServer", // Exclusion list templates
"Workstation"
]
}
Operational Settings
{
"CA-OPS-002": ["10", "3", "5", "1"], // Certificate expiration limits
// [Root Max, Root Min, Sub Max, Sub Min]
"CA-OPS-003": true, // AIA validation required
"CA-OPS-004": true, // CDP validation required
"CA-OPS-005": true, // AIA reachability validation
"CA-OPS-006": true, // CDP/CRL reachability validation
"CA-OPS-007": true, // AIA certificate validation
"CA-OPS-008": true, // CRL download validation
"CA-OPS-009": 127 // Audit filter threshold
}
Permission Settings
{
"CA-PERM-001": [ // Expected CA administrators
"DOMAIN\\CA-Admins", // Substitute DOMAIN in parameters.json
"DOMAIN\\PKI-Admins"
]
}
Custom Control Configuration
Enabling/Disabling Controls
Controls can be enabled or disabled via parameters.json:
- Boolean values:
trueto enable,falseto disable - Numeric values: Non-zero to enable,
0to disable - Array values: First element controls enablement
Threshold Configuration
Many controls support configurable thresholds:
- Key sizes (CA-CRYPTO-001, CA-TEMPLATE-002)
- Expiration limits (CA-OPS-002)
- Algorithm lists (CA-CRYPTO-002)
- Schema versions (CA-TEMPLATE-003)
Exclusion Lists
Some controls support exclusion lists:
- Template exclusions (CA-TEMPLATE-005)
- Administrator principals (CA-PERM-001)
Script Customization
PowerShell Scripts
The tool uses helper PowerShell scripts for certain operations:
helper/ca-config-001.ps1– Registry configurationhelper/ca-config-006.ps1– Template export
These can be customized for specific environments or requirements.
Evidence Parsing
The tool includes sophisticated evidence parsing for:
- JSON configuration files
- certutil command output
- PowerShell object output
- Registry data structures
Security Considerations
Data Handling
Information Collected
The tool collects and stores:
- Certificate Authority configuration data
- Certificate templates and settings
- Cryptographic algorithm information
- Network connectivity information
- Permission and security settings
Storage Security
- All data stored locally in Audit-Results directory
- No sensitive information transmitted externally
- Evidence files contain security assessment data
- Downloaded certificates and CRLs stored for analysis
Network Security
Communication Methods
- WMI: Uses DCOM/RPC over port 135
- PowerShell: Uses WinRM over ports 5985/5986
- LDAP: Active Directory queries over port 389/636
- HTTP/HTTPS: URL reachability testing
Security Recommendations
- Use dedicated audit accounts with minimal privileges
- Implement network segmentation for CA servers
- Use encrypted channels where available (LDAPS, WinRM HTTPS)
- Regularly review and update audit permissions
Credential Usage
Authentication Methods
- Uses current user credentials for all operations
- No credential storage or caching
- Relies on Windows integrated authentication
Best Practices
- Use dedicated service accounts for auditing
- Implement principle of least privilege
- Regularly rotate audit account credentials
- Monitor audit account usage
Compliance Support
Regulatory Frameworks
The tool supports compliance with:
- NIST SP 800-53: Security controls assessment
- PCI DSS: Certificate and cryptographic requirements
- ISO 27001: Information security management
- CIS Benchmarks: Security configuration guidelines
Evidence Generation
- Detailed control execution evidence
- Timestamped execution records
- Compliance status reporting
- Remediation recommendations
Appendix
Control ID Reference
Connectivity Tests
- PKI-TEST-001: WMI/SMB Connectivity Test
- PKI-TEST-002: PowerShell Connectivity Test
- PKI-TEST-003: User Privilege Validation
Configuration Audits
- CA-CONFIG-001: CA Registry Configuration
- CA-CONFIG-002: CA Templates
- CA-CONFIG-003: AIA Configuration
- CA-CONFIG-004: CRL Distribution Points
- CA-CONFIG-005: CAPolicy.inf Configuration
- CA-CONFIG-006: PowerShell Template Export
Operational Audits
- CA-OPS-001: CertSvc Service Status
- CA-OPS-002: CA Certificate Expiration Validation
- CA-OPS-003: CA Certificate AIA Configuration Validation
- CA-OPS-004: CA Certificate CDP Configuration Validation
- CA-OPS-005: AIA URL Reachability
- CA-OPS-006: CDP/CRL URL Reachability
- CA-OPS-007: AIA Certificate Download and Expiration Validation
- CA-OPS-008: CRL Download and Validation
- CA-OPS-009: CA Audit Filter Configuration
Template Audits
- CA-TEMPLATE-001: CA Template Restriction Validation
- CA-TEMPLATE-002: Template Key Size Validation
- CA-TEMPLATE-003: Template Schema Version Validation
- CA-TEMPLATE-004: Template CSP Validation
- CA-TEMPLATE-005: Template Enrollee Supplies Subject Validation
Cryptographic Audits
- CA-CRYPTO-001: CA Certificate Key Size Validation
- CA-CRYPTO-002: CA Certificate Weak Algorithm Detection
- CA-CRYPTO-003: CA Certificate Extended Key Usage Validation
- CA-CRYPTO-004: CA Certificate Basic Constraints Validation
Permission Audits
- CA-PERM-001: CA Administrator Permission Validation
Severity Levels
Critical
- Immediate security risks
- System availability impacts
- Fundamental security failures
High
- Significant security concerns
- Compliance violations
- Important configuration issues
Medium
- Moderate security risks
- Best practice deviations
- Configuration improvements needed
Low
- Minor security observations
- Informational findings
- Enhancement opportunities
Status Codes
Success
Control executed successfully and met expected results.
Failure
Control executed successfully but did not meet expected results.
Error
Control failed to execute properly due to technical issues.
Not Run
Control was skipped (typically due to prerequisite failures).
File Structure
Output Structure
Audit-Results/
├── PKI-Audit.json (Complete results)
├── PKI-Audit.csv (Summary data)
├── *.cer (Certificate files)
├── *.crl (CRL files)
├── *.txt (Evidence files)
└── *.json (JSON evidence files)
Support and Resources
Documentation
- This User Guide
- In-application help (
--helpoption) - Control-specific evidence files
Technical Support
- Contact: [email protected]
- Website: https://securetron.net
- Product: https://securetron.net/pki-trust-auditor/
Updates and Maintenance
- Regular security updates
- New control additions
- Performance improvements
- Compatibility updates