Wireless Authentication using Certificates
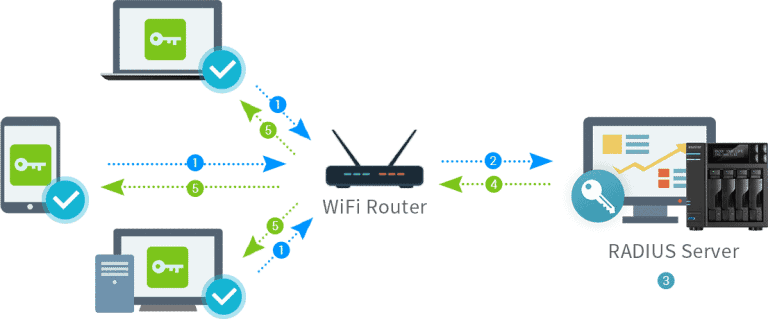
Certificates for wireless authentication are a critical component of securing wireless networks, particularly in enterprise environments. They are used to establish trust between devices and the network, ensuring that only authorized users and devices can connect. Below is an overview of how certificates are used for wireless authentication:
Types of Wireless Authentication Using Certificates
a. WPA2-Enterprise / WPA3-Enterprise
-
These standards use 802.1X/EAP (Extensible Authentication Protocol) for authentication.
-
Certificates are used to authenticate both the client (user/device) and the server (RADIUS server or authentication server).
-
Common EAP methods that use certificates include:
-
EAP-TLS (Transport Layer Security): Uses X.509 certificates for mutual authentication.
-
EAP-TTLS (Tunneled Transport Layer Security): Can use certificates for server authentication and other methods (e.g., passwords) for client authentication.
-
PEAP (Protected EAP): Uses a server-side certificate to create a secure tunnel, with client authentication typically done via passwords or other methods.
-
b. BYOD (Bring Your Own Device)
-
Certificates can be issued to personal devices to allow secure access to corporate wireless networks.
-
This is often managed through Mobile Device Management (MDM) solutions or certificate provisioning systems.
c. IoT Devices
-
Certificates are used to authenticate IoT devices connecting to wireless networks, ensuring they are trusted and secure.
Components of Certificate-Based Wireless Authentication
a. Certificate Authority (CA)
-
A trusted entity that issues and manages digital certificates.
-
The CA signs the certificates used by both the client and the server, establishing a chain of trust.
b. Client Certificates
-
Installed on user devices (e.g., laptops, smartphones, IoT devices).
-
Used to prove the identity of the device or user to the authentication server.
c. Server Certificates
-
Installed on the RADIUS server or authentication server.
-
Used to prove the identity of the server to the client device.
d. RADIUS Server
-
Handles the authentication process, verifying the client’s certificate and ensuring it matches the CA’s trust chain.
e. Wireless Access Point (AP)
-
Acts as the intermediary between the client device and the RADIUS server, forwarding authentication requests.
How Certificate-Based Authentication Works
a. Client Connects to the Network:
- The client device attempts to connect to the wireless network.
- The access point requests authentication
b. Certificate Exchange:
- The client presents its certificate to the RADIUS server.
- The RADIUS server presents its certificate to the client.
c. Mutual Authentication:
- Both the client and server validate each other’s certificates using the trusted CA.
- If the certificates are valid, the authentication proceeds.
d. Secure Connection Established:
- Once authenticated, the client is granted access to the network.
- Encryption keys are exchanged to secure the wireless communication.
Benefits of Using Certificates for Wireless Authentication
-
Strong Security: Certificates provide strong encryption and mutual authentication, reducing the risk of unauthorized access.
-
Scalability: Certificates can be easily deployed to a large number of devices, making them ideal for enterprise environments.
-
No Password Management: Eliminates the need for password-based authentication, reducing the risk of credential theft.
-
Compliance: Meets regulatory requirements for secure authentication (e.g., PCI DSS, HIPAA).

Challenges of Using Certificates
-
Complexity: Setting up and managing a PKI (Public Key Infrastructure) can be complex.
-
Certificate Lifecycle Management: Certificates must be issued, renewed, and revoked as needed.
-
Device Compatibility: Some older devices may not support certificate-based authentication.
Best Practices for Implementing Certificate-Based Wireless Authentication
-
Use a Trusted CA: Ensure your certificates are issued by a reputable Certificate Authority.
-
Automate Certificate Deployment: Use MDM or network access control (NAC) solutions to automate certificate provisioning.
-
Monitor and Renew Certificates: Implement processes to track certificate expiration and renew them promptly.
-
Secure Your PKI: Protect your CA and private keys to prevent compromise.
-
Test Compatibility: Ensure all devices and systems support the chosen EAP method and certificate format.
- Use Best Tools: PKI Trust Manager for issuing and managing certificates in various environments.